Patch management supports patch updates for Windows and Linux devices, providing:
- Partner- and customer-level visibility across the infrastructure to easily supervise all patch management activities.
- Management from a central location for easy enablement, patch approval, monitoring, access, and notification.
- Custom job scheduling for running third-party patch automation scripts.
- Custom configuration that minimizes manual intervention.
- Custom scripts using the Run Book Automation (RBA) feature for Windows and Linux, making RBA scripts available at the partner and customer levels for optimum control.
- Detailed, scheduled reports showing patch metrics.
You assign devices using the resources device management assign job policies when creating a patch scan or setting up a patch configuration.
Constraints
- You can patch only with agents.
- There is no patching support for the Linux gateway.
- Auto-approval is applicable only for Windows patching. Patches must be manually approved for Linux devices.
- There is no patching support when using third-Party applications.
- There is no patching support with third-party integrations.
Patching concepts
Patch feed
A patch feed is a source of published patch information including all the available patch attributes. You can get a patch feed from an OS vendor, a software package provider, or a partner who manages published packages.
A typical patch feed includes the following information:
- The patch details such as patch name, patch ID, severity, OS Version, and release date.
- Patch rating for rated patches.
- CVE ID, if provided.
Patch baseline
A Patch baseline can help you determine the approved patches for your resources.
Patch compliance
Patch compliance checks for compliance of selected devices or device groups against configured patch baselines. A patch compliance check job automatically computes patch compliance after every patch scan run on a device.
Patch rating
A patch rating provides a way to prioritize patch updates.
Patch Status
Patch status tracks patch status of patches in the patch configuration:
- Installed
- In Progress
- Failed
The In Progress status indicates the number of in-progress patch installations that are not yet fully installed.
Patch process flow
Patch management permits you to scan, approve, configure, and install software patches before deployment. The following figure shows an example of processing a Microsoft patch list:
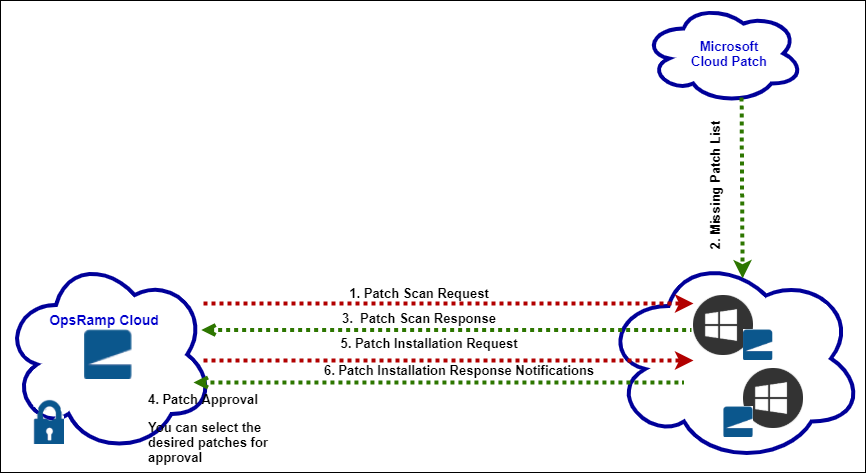
Steps 1, 2, and 3: Patch scan
The patch scan request gets the latest updates for the different Windows and Linux versions. After installing the agent, a job automatically starts that gets the list of missing patches. You create jobs to scan for the missing patches.
Step 4: Patch approval
After getting the missing patches, you approve the patches you want to install. You can manually approve patches or enable Auto-Approve to automatically approve security and critical whitelisted patches. Using a whitelist, you can approve patches globally by selecting several devices at a time. You can also rate patches.
Audit trails are recorded for all patch approvals along with patch notifications.
Steps 5 and 6: Patch configuration and installation
The approved ID list is sent to the agent for installation. Use the patch installation schedule to help set the installation time and the patch sources. Configure the patches in your devices depending on the Approval Type, Reboot Options, and Patching Schedule. Patches can be installed on demand.
You can select users to get notifications on patch management actions, including configuration and approval.
Patch management widgets
Dashboard patch management widgets provide a snapshot of the current patch status in your Windows and Linux devices:
| Widget | Description |
|---|---|
| Patch Compliance | Compliance status of a set of devices for a specific baseline. |
| Patch Pending Approvals | Number of patches pending approval. |
| Patch Status | Device count categorized by patch installed, pending approved critical and security patch installation. The widget displays the results of the most recent patch scan within the last 30 days. |
View patch-related alerts
The agent sends an alert to the alert browser and displays a pending reboot after patching completion.
The following alert types are generated during patch scan, configuration, and approval:
| Alert Type | Description |
|---|---|
| Initiate | Patch scan is initiated. |
| Search | Missing Patches found and approved. |
| Download initiated | Patches are downloaded from the Microsoft server and WSUS. |
| Install complete | Installation is completed successfully. |
To reiterate how to view the generated alerts using the alert browser:
- Open the alert browser.
- Select the ID to view the different types of generated alerts.
To view the generated alerts using the Alerts tab:
- Select a client from the All Clients list.
- Go to Alerts > Manage Views.
- Click Add.
- Select the attributes and click Apply to displays the list of alerts.
FAQs
How can I find the missing patches for the devices?
Create and a run a missing patches request job to identify missing patches.
What are the different types of approvals?
- Auto approve: Automatically approve patches. Auto approval is applicable to Windows only.
- Manual approval: Manual approval is needed to install a patch.
What happens when the device fails during the patch window?
The devices must be up and running to take any action.
What happens if the patch fails?
If the patch fails, a critical alert is raised with a reason for the failure.
When happens when the device needs to be rebooted after patching?
If configured to reboot servers after patching, the following message is displayed:
Patching completed and need to reboot.You can ignore the reboot if automatic reboot is not enabled.
What is the reason to create a job?
Use a job to gather missing patch details from the servers configured at the device.
What is the reason for the mismatch between local machine patches and server patches?
Confirm that the server settings are a Microsoft server or WSUS server, local.
Are incidents created during patching?
No, Incidents are not created during patching.