Introduction
Clients are the end-level entities that use the platform to access and manage IT services.
Creating a client in OpsRamp establishes a dedicated and secure environment where end-users - such as public sector entities, subsidiaries, or enterprise customers - can manage their own IT infrastructure. Each client has autonomy to control their resources, configure monitoring policies, assign users, and set up automation based on specific operational needs.
This approach empowers clients to operate independently while still adhering to governance structures defined by the partner. It supports scalability, maintains data isolation, and ensures that services are delivered with clarity and accountability.
Clients benefit from OpsRamp’s robust capabilities in monitoring, alerting, and incident management, enabling them to maintain system health and business continuity efficiently.
Create a client
The following video guides you through the process of creating a Client in OpsRamp.
Navigate through the tabs below and provide the information in each section to complete the client setup.
ACCOUNT
The Account section has critical information and settings about your client. It allows you to manage personal information like Name, Notification Email, and other contact details.
- Click Setup > Account. The ACCOUNT DETAILS screen is displayed.
- Click Clients tile.
- Click +ADD in CLIENTS LIST screen. The ADD CLIENT screen is displayed.
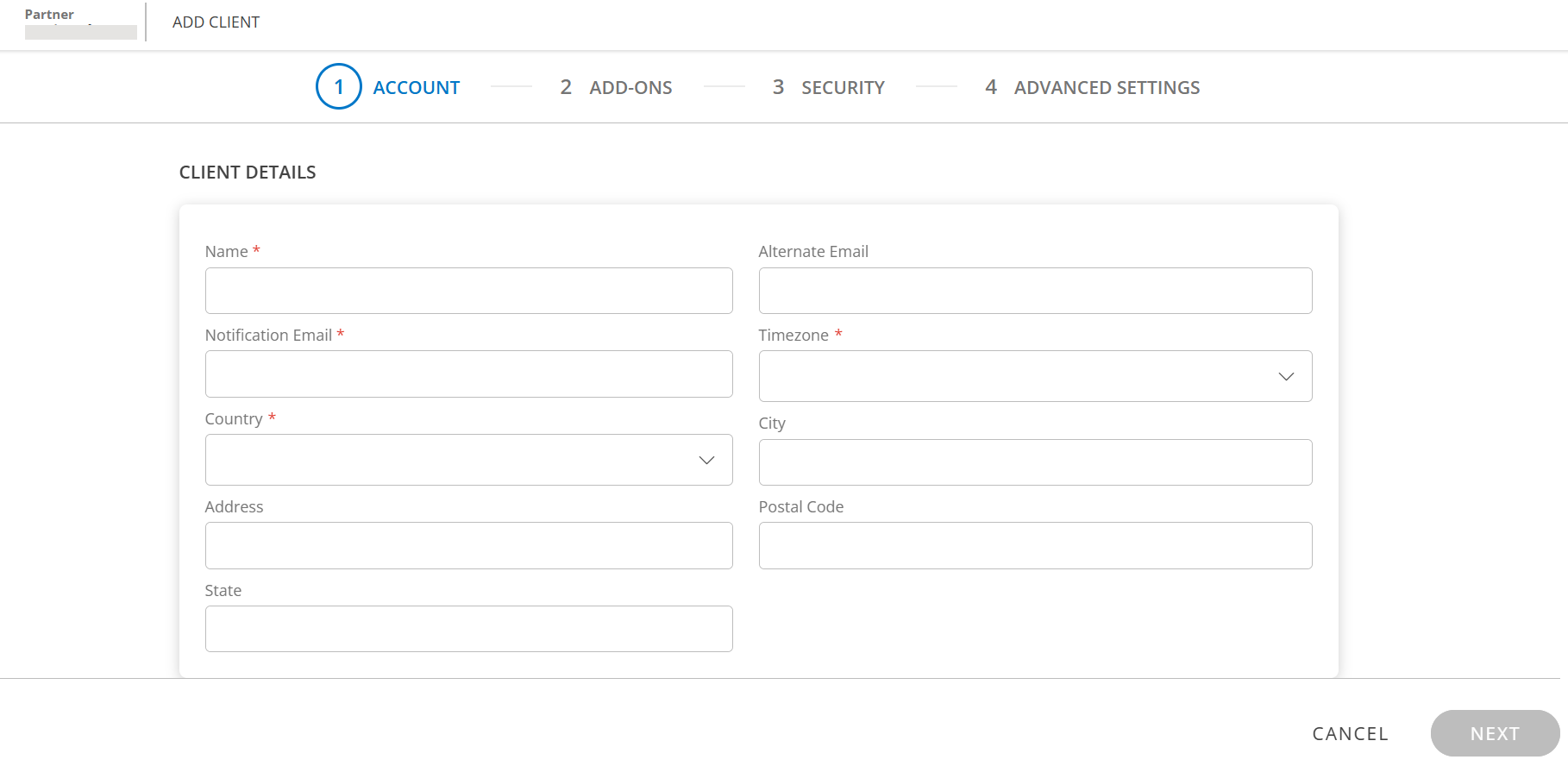
- Enter the following information.
CLIENT DETAILSField Name Field Type Description Name String Name of the client. Alternate Email String Alternate Email address of the client. Notification Email String Client Email address. Timezone Dropdown Timezone of the client. Country Dropdown Country where the client is located. City String City of the client. Address String Address of the client. Postal Code Integer Postal code State String State in which the client is located. - Click NEXT.
ADD-ONS
The Add-Ons tab lists the Product Packages and Add-Ons.
Select one or more of the following packages as per the operational requirement to monitor the infrastructure:
- Hybrid Discovery and Monitoring (default)
- Event and Incident Management
- Remediation and Automation
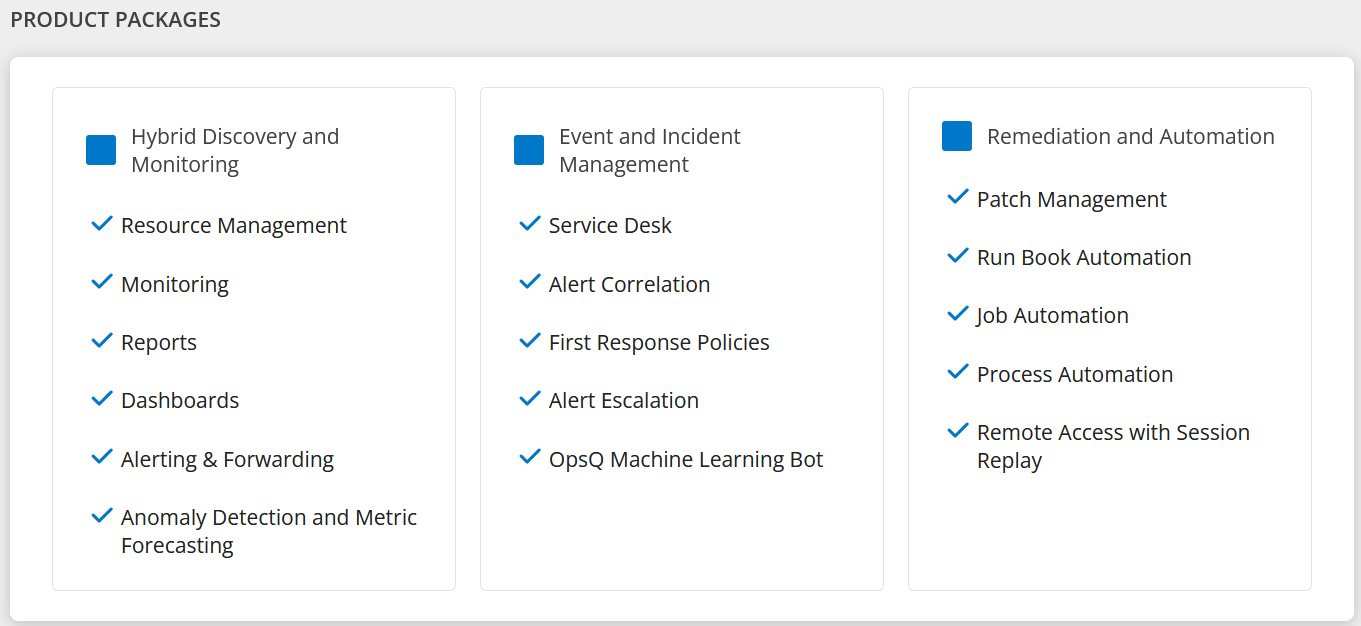
Choose the packages that match the requirements.
Based on the packages you select, the Add-Ons are displayed. If you keep only Hybrid Discovery and Monitoring, Adapter Integrations, Extended Data Retention, Mask Resource Identity Management, Offline Alerts, Log Management, and Trace Management are added as Add-Ons.
Hybrid Discovery and Monitoring package
A broad range of IT resources across data center, public cloud, and cloud native environments can be discovered and monitored with agent-based and agentless monitors. These include:
- Data center applications, URLs, containers, servers, and network resources.
- Public cloud environments of compute instances, databases, load balancers, and PaaS services.
- Cloud native environments with containers and orchestrators.
Built-in monitors are provided that capture availability and performance metrics and observer optimal threshold limits for supported resources. You can extend the platform to monitor any kind of IT resource by writing custom monitor scripts.
The Hybrid Discovery and Monitoring package includes the following modules:
- Resource Management
- Monitoring
- Reports
- Dashboards
- Alerting & Forwarding
- Anomaly Detection and Metric Forecasting
Event and Incident Management package
The Event and Incident Management package leverages proprietary event correlation algorithms, incident creation, and machine learning-powered alerts. The package includes:
- Service Desk
- Alert Correlation
- First Response Policies
- Alert Escalation
- OpsQ Machine Learning Bot
Remediation and Automation package
The Remediation and automation package implements patch job scheduling, remediation task execution, and resource maintenance using a remote console. The package includes:
- Patch Management
- Run Book Automation
- Job Automation
- Process Automation
- Remote Access with Session Replay
Add-ons
Following are the Add-Ons for Hybrid Discovery and Monitoring package: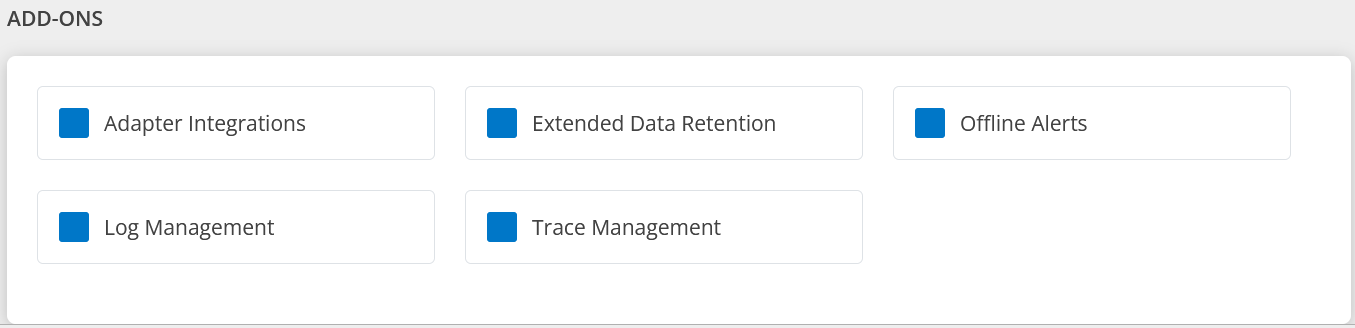
Adapter Integrations – This add-on is used to enable Adapter category Apps, to perform discovery and monitoring of the end device.
Refer Compute, Network, Storage sections under Integrations
Extended Data Retention - You can retain the asset data for 12 months.
Offline Alerts - If any resource goes to an unknown state, an alert will be triggered.
Log Management - Collect, store, analyze and monitor all log data that is generated by the resources, applications, and services effortlessly.
Trace Management - Track all requests and transactions as they interact with various components of the infrastructure. This ensures end-to-end monitoring of the transactions and helps identify root causes of the issues.
Event and Incident Management
Events represent business-impacting issues that require a response. Event and incident management uses escalation policies to aggregate, interpret, and act on events detected by monitors, resource diagnostics, and third-party integrations.
Using service maps, you can visualize the relationship between monitored resources and assess business and user impact based on resource health.
Event interpretation and response can be automated. Automation correlates and suppresses alerts, notifies users, and creates incident tickets for alerts that need operator intervention.
Add-ons
Following are the Add-Ons for Event and Incident Management package: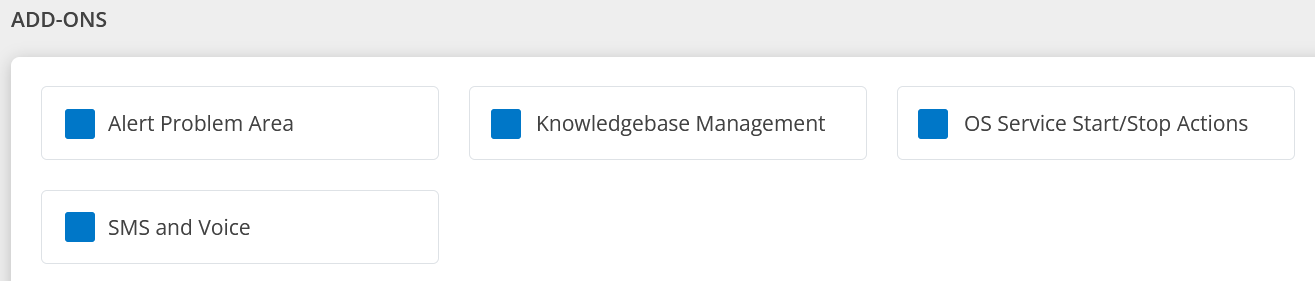
Alert problem area – Alert Problem Area enriches the alert Problem Area field with information extracted from the alert subject or description. Alert Problem Area is usually used for log-type alerts where rich information is embedded in the alert subject or description, but the metric value is the generic metric name. If the Problem Area field is not enriched, it defaults to the alert Metric field value.
See Alert Problem Area for more information.
Knowledge Base Management - Capture product information, operational procedures, and frequently asked questions, providing a reference source for the organization.
See Knowledge Base for more information.
OS Service Start/Stop Actions - This add-on provides the ability to start and stop the OS services on agent-installed devices when required permissions are given.
Navigation: Infrastructure > Resources Details > Services.SMS and Voice - This is a paid add-on, and when enabled will send notifications through SMS and Voice.
Remediation and Automation
Automate operational tasks that respond to events or execute routine maintenance activities. Automation workflow capabilities permit you to compose workflows that are tailor made for your use cases.
Event remediation and automation can be automated by composing workflows to handle events. This includes SMS, Voice, and Email notifications. Remote SSH is also supported for alert resolution.
Add-ons
Following are the Add-Ons for Remediation and Automation package: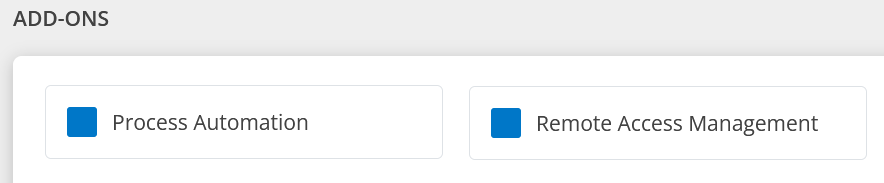
Process Automation - This add-on provides the ability to define and execute process automation tasks.
See Process Definition for more information.
Remote Access Management - This is used to enable remote access (RDP, SSH, Telnet) to managed devices.
See Remote Consoles for more information.
Contact Support to change the add-on permission.
Remediation and automation package
The following are unavailable if you opt not to subscribe to this package:
Application Patch Management add-on
Automation option in the Workspace drop-down menu
These permission sets:
- Jobs
- Consoles
- Patch Approvals
- Recording Audits
- Scripts
- Commands
Selecting a client that is not subscribed to the Remediation and Automation package generates the following warning on the Alerts, Service Desk, and Automation screens:
Access Denied! The client is not subscribed to this product package.
Event and Incident Management package:
The following are unavailable if you opt not to subscribe to this package:
Event Enrichment, Scheduled Task, SLA, and SMS & Voice add-ons
The Alerts menu option in Setup (Setup > Alerts)
These permission sets:
- OpsQ
- Incident
- Change Request
- Task Request
- Service Request
- Problem
- Time-bound request
Selecting a client that is not subscribed to the Event and Incident Management package generates the following warning on the Alerts, Service Desk, and Automation screens:
Access Denied! The client is not subscribed to this product package.
- Click NEXT.
SECURITY
Security feature ensures effective Access Management and stringent Password Policy Settings. Access Management allows you to restrict specific IP addresses, implement two-factor authentication for improved security. Password Policy Settings enables you to implement strict password settings thereby preventing unauthorized access and security breaches.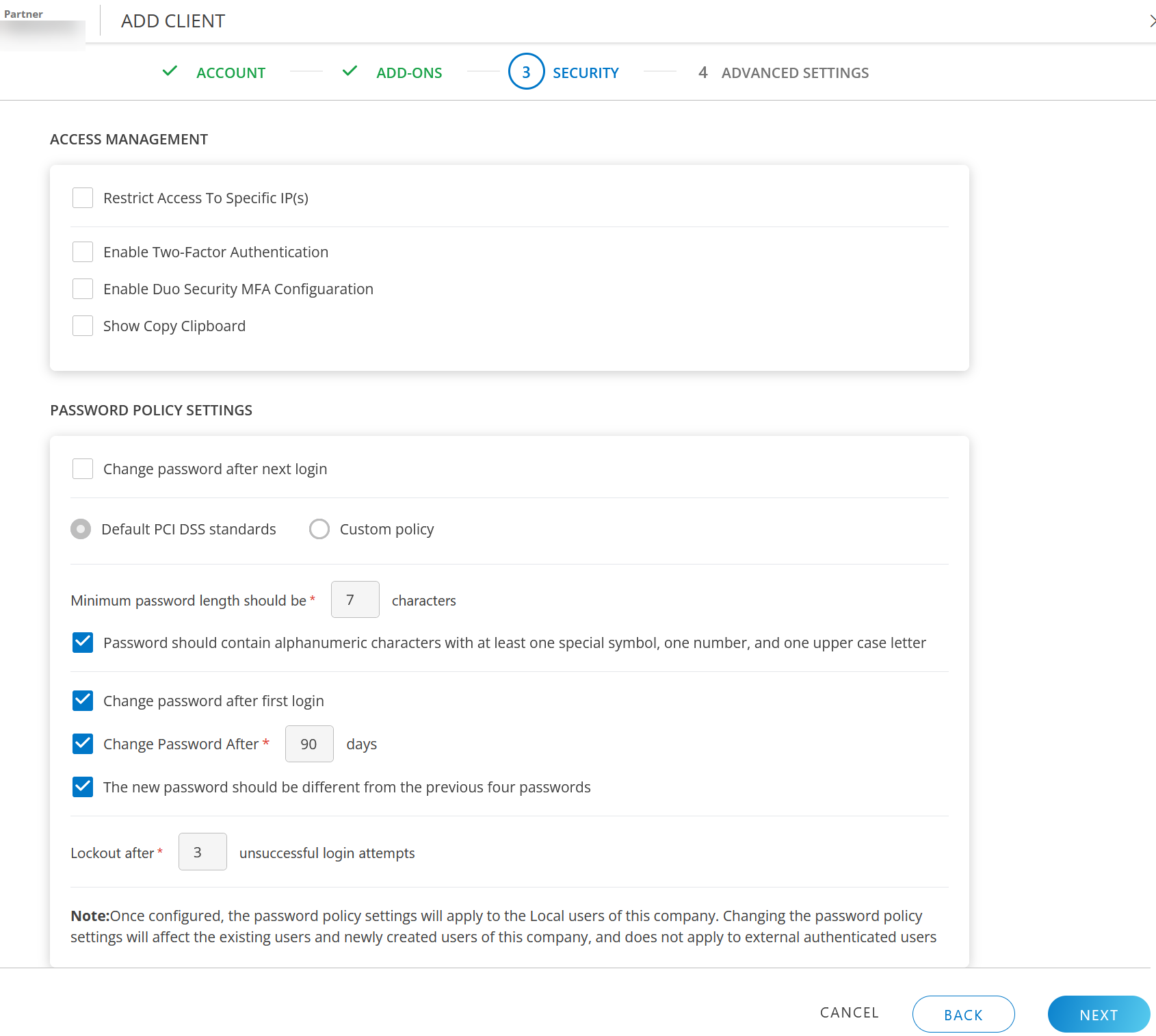
ACCESS MANAGEMENT
Access Management in OpsRamp includes features such as enhanced security with Two-Factor Authentication and Duo Security MFA Configuration, restricting access to specific IP addresses, and enabling the Show Copy Clipboard functionality thereby enhancing usability.
Select one or more of these options as per the requirements:
Restrict Access to Specific IP(s): Restricting access to specific IP addresses can reduce security issues. Enter the IP Addresses separated by comma.
The following error message is displayed when you attempt to log into the platform from an IP address other than those permitted:Your organization policies restrict you from accessing OpsRamp from your current IP.Enable Two-Factor Authentication: Select the checkbox to enable two-factor authentication. See Two-Factor Authentication for more details.
Enable Duo Security MFA Configuration: Select the checkbox to enable Duo Security.
- Enter the Integration Key, Secret Key, API hostname in the DUO SECURITY MFA CONFIGURATION dialog box and click SAVE. The details are displayed.
- Enter the Integration Key, Secret Key, API hostname in the DUO SECURITY MFA CONFIGURATION dialog box and click SAVE. The details are displayed.
Show Copy Clipboard: Select the checkbox to enable Show Copy Clipboard.
PASSWORD POLICY SETTINGS
The Password Policy Settings section allows you to configure password policy, which once configured will apply to all the users of the client.
Change password after next login: Select this option, if you want to change password after next login. This means that all the users of the organization will mandatorily have to change their passwords after they login for the first time. This change will make all login sessions inactive.
Note: It is recommended not to change the password policy frequently, as this will affect the existing and newly created users of your organization, and will not apply to external authenticated users.
You can opt for Default PCI DSS standards or Custom policy.
Default PCI DSS standards: Select this checkbox to apply default PCI DSS standards. You cannot modify the settings.
Custom policy: Select this checkbox and configure the policy settings as per your organizational needs.
- Click NEXT.
ADVANCED SETTINGS
The Advanced Settings section allows you to configure options designed to optimize the management and monitoring capabilities of your client’s IT infrastructure. These settings enable you to have greater control over aspects such as availability, integration settings, log management, NOC for alert management, remote access management, and root cause analysis through alerts and logs.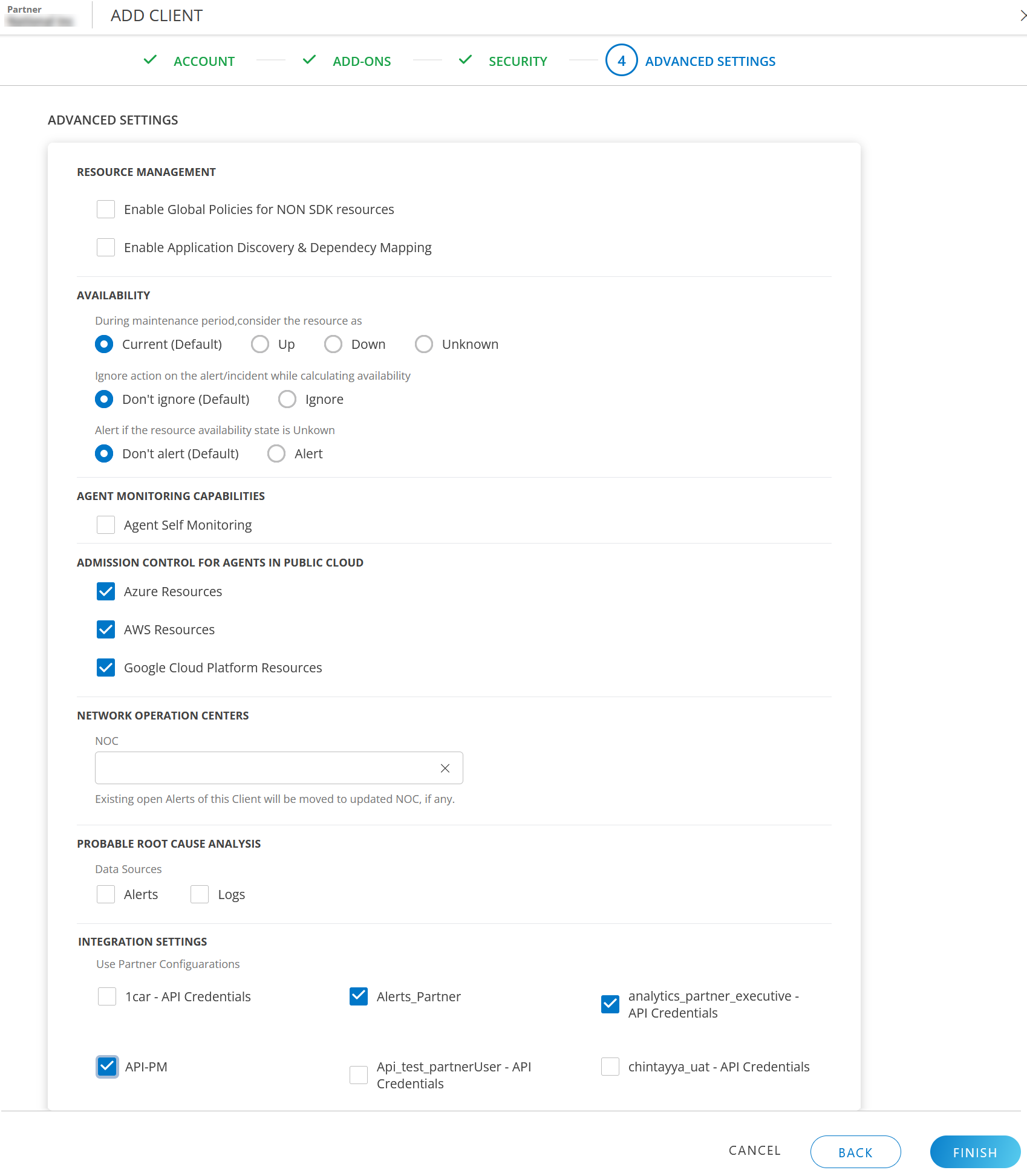
RESOURCE MANAGEMENT
- Select these options as per your requirements:
Enable Global Policies for NON SDK resources: Select the checkbox to enable global policies for the client.
This flag is considered for non-SDK based resources.
For SDK based resources, regardless of whether this checkbox is enabled or disabled, the Device Management Policies will be automatically applied.
Enable Application Discovery & Dependency Mapping: Select the checkbox to enable application discovery and dependency mapping.
AVAILABILITY
During maintenance period, consider the resource as: By default, the current state is selected.
Select the state of the resources during scheduled maintenance period.
If you select the state as Up, during scheduled maintenance period the state of the resource(s) will be displayed as Up, even if your resource(s) is powered off / restarted.Ignore action on the alert/incident while calculating availability: By default, Don’t ignore option is selected.
Select an option as per your requirements. If you select Ignore, the system will ignore actions on the alerts or incidents that are suppressed, acknowledged, etc., when resource availability is calculated.Alert if the resource availability state is Unknown: By default, Don’t alert option is selected.
Select Alert option, if you want to receive alerts if the availability state of the resource is UNKNOWN.
AGENT MONITORING CAPABILITIES
Select the Agent Self Monitoring option to enable agent self monitoring.
- Choose a time-frequency from the dropdown (supported time frequencies are 1, 2, 3, 6, and 12 hours).
ADMISSION CONTROL FOR AGENTS IN PUBLIC CLOUD
Select these options to enable onboarding AWS, Azure, and Google Cloud Platform Resources, using agent without public cloud integration.
NETWORK OPERATION CENTERS
Select NOC from the dropdown. All the existing open alerts will be moved to the NOC.
PROBABLE ROOT CAUSE ANALYSIS
Select Alerts or Logs or both, as Data Sources.
Alerts: If you select Alerts, the system will consider alerts generated to aid in root cause analysis.
Logs: If you select Logs, the system will consider log data from various sources for root cause analysis.
INTEGRATION SETTINGS
Select one or more available custom integrations that you can inherit from the partner’s configurations.
- Click FINISH. The client is successfully created and a confirmation message appears.
The client details are displayed in the CLIENTS LIST screen in a tabular form.
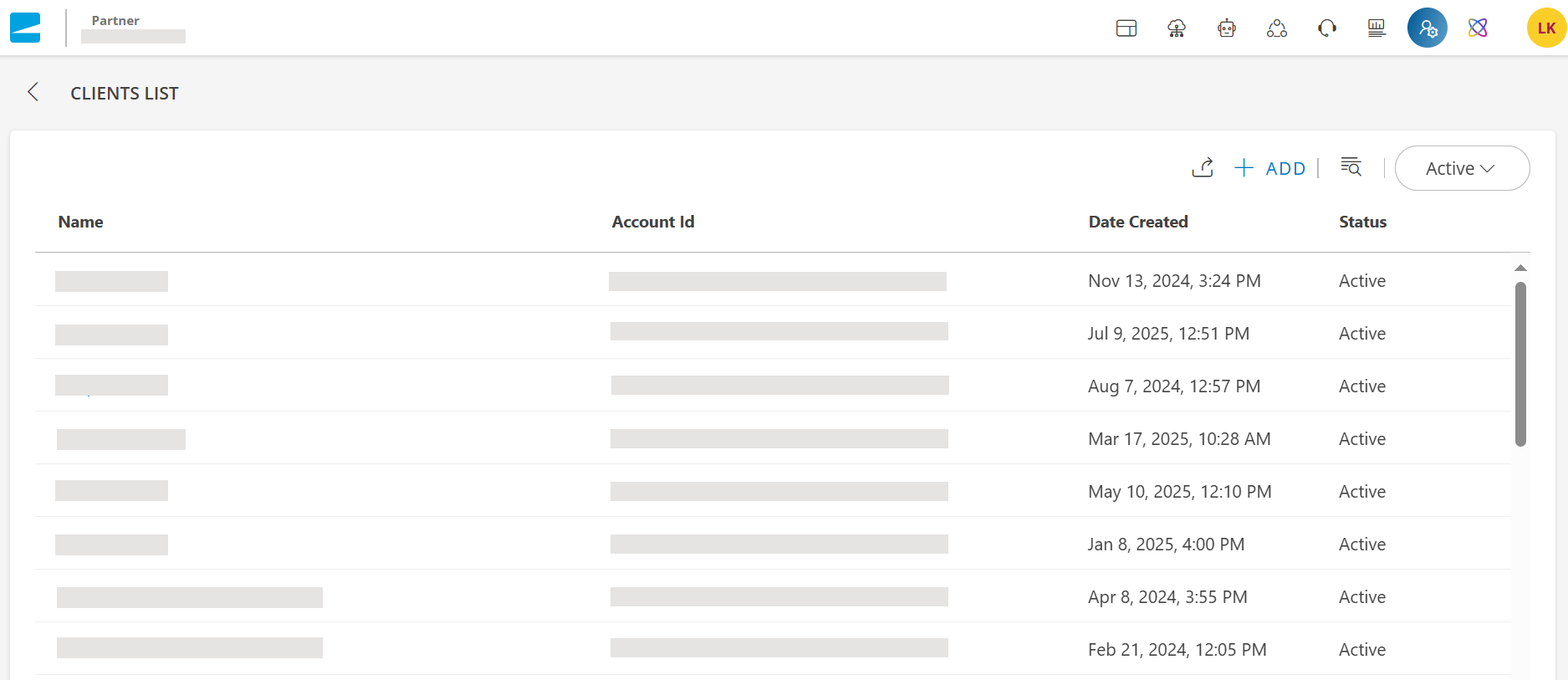
Table below shows the columns with their description:
| Field Name | Description |
|---|---|
| Name | Name of the client. |
| Account Id | Account Id of the client. |
| Date Created | The date on which the client was created. |
| Status | The current status of the client. |
Related Topics
- See View and edit client details to learn how to view and update a client’s configuration.