As a SaaS ITOM platform, the confidentiality, integrity, and availability of critical data are ensured.
A standards-based security architecture is implemented, which guarantees the highest levels of security, control, availability, and scalability.
Security is implemented in the following areas:
- Agent
- Gateway
- Cloud
- Operations
Agents and gateways
Agents are installed on customer target resources on a private network. There are two kind of Agent installations:
- Proxy Agent: The agent needs outgoing communication with the gateway on port 3128, the HTTP proxy server. Using the proxy server, the agent establishes a connection with the cloud and uses a secured tunnel based on TLS 1.2.
- Direct Agent: The agent establishes a connection with the cloud and uses a secured tunnel based on TLS 1.2.
Gateways are virtual appliances that collect data from the managed environment, which have the following characteristics:
- Sit in a client internal environment with a private IP behind the firewall.
- Establish a secure connection to the Cloud over the internet using a secured tunnel based on TLS 1.2.
Agent properties
| Property | Description |
|---|---|
| Function | A lightweight agent that runs on Windows and Linux systems in the managed environment.
|
| Form factor | Windows and Linux binaries:
|
Gateway properties
| Property | Description |
|---|---|
| Access controls | All configuration updates for the gateway are pushed from the cloud using an encrypted channel created by the gateway. |
| Operating System | Hardened configuration of Ubuntu Server. Hardening includes the following measures:
|
| Form Factor | The gateway is a virtual appliance that runs on a hypervisor. |
Connectivity requirements
The requirements for connectivity include:
| Property | Description |
|---|---|
| Outbound | Agents and gateways require outbound network connectivity to the cloud. If your organization has firewall policies that limit outbound access to specific IP addresses, agents and gateways must have access OpsRamp IP addresses. |
| Inbound | N/A - There are no inbound connectivity requirements. |
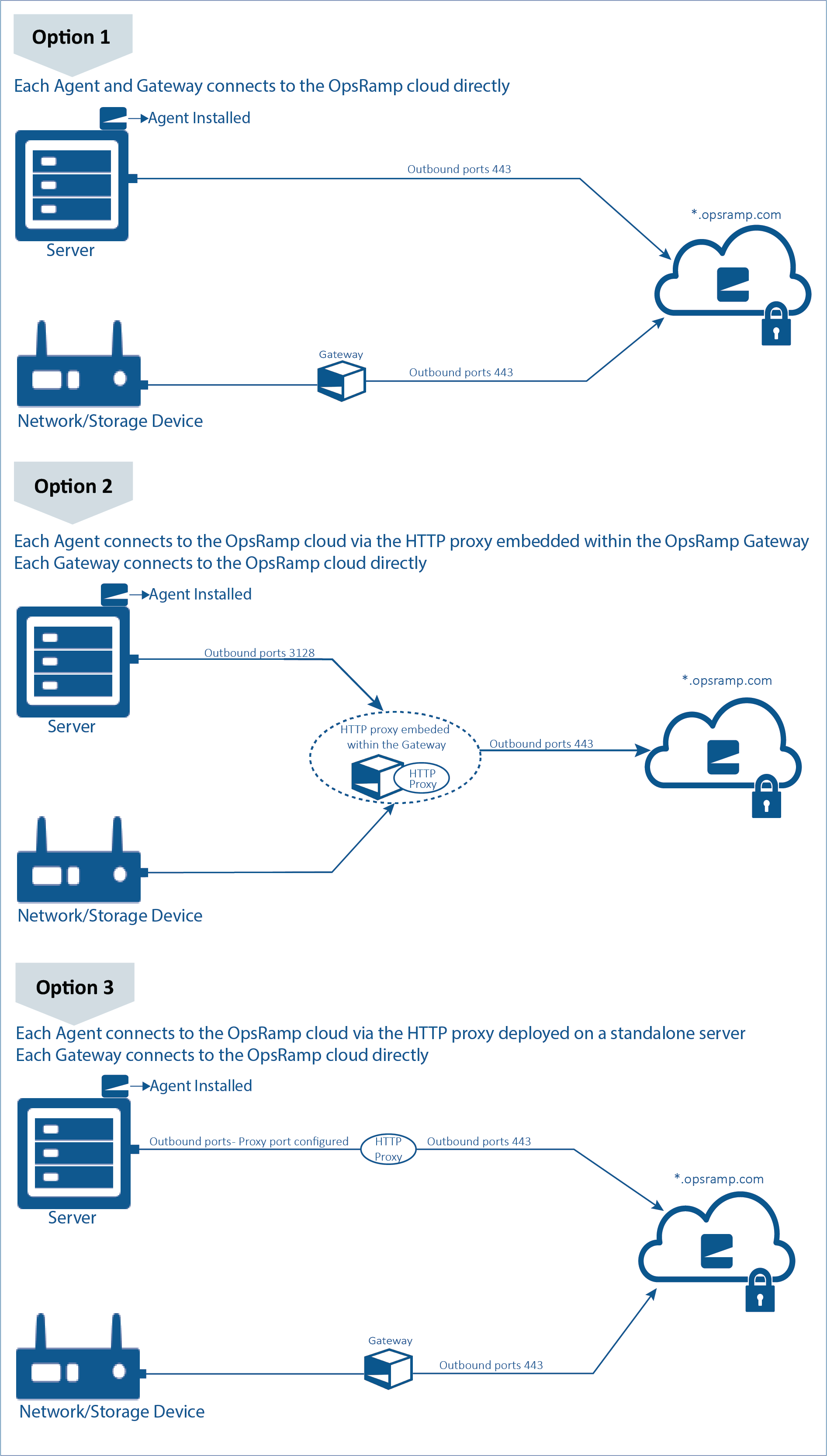
Configuration options
The following diagram shows the configuration options:
- Agent and gateway both have a direct connection to the cloud.
- Each agent has an HTTP proxy connection to the gateway and each gateway has a direct connection to the cloud.
- Each agent has an HTTP proxy connection deployed on a standalone server and each gateway has a direct connection to the cloud.
Agents work with standard HTTP Proxy.
Data collection
Data is collected and stored only as needed for IT operations management functions on the devices it manages.
Data is not collected and stored from monitored applications, including data in database tables, application transaction contents, and user credentials.
| Data Type | Data Collected | Data Storage and Security |
|---|---|---|
| Performance statistics | System-level information needed to monitor the performance and health of managed devices:
| Device performance statistics are stored only in the cloud. The agent and gateway collect and transmit this data to the Cloud. |
| Events and SNMP traps | Operating System events and traps generated by SNMP agents. | The gateway and Agent process events and traps locally and send resulting alerts to the Cloud using a secure channel. Raw event data is not stored in the Cloud. |
| Resource configuration and metadata | System-level information needed to asset device configuration status:
| The gateway and Agent send configuration data to the Cloud using a secure channel |
| Device Credentials | Credentials (username/password) needed to discover devices, access performance and configuration data, and log into devices to run automation scripts. | The IT administrator provides device credentials using its user interface. Device credentials are stored in the Cloud, using industry-standard 2048-bit RSA encryption. |
| Logs and Traces | Data collected as part of logs and traces includes information from application logs, system logs (syslogs), and activity logs, particularly in cloud environments. Logs automatically capture all content written to the configured log file for ingestion.Personal Information: If the log file contains sensitive or personal information, users should mask the sensitive data to protect it before ingestion. This ensures compliance with security and privacy standards while preventing exposure of confidential information. | Storage: The collected data is stored in the secure storage engine with restricted access to the backend. Users with logs_view or trace_view permissions can access and view logs or traces directly from the portal. |
Data management
| Property | Description |
|---|---|
| Data classification | Only required data is collected and stored for IT operations management on managed devices and applications. Data collected data is limited to device performance metrics, performance and failure events, and configuration information. |
| Data isolation | Strict multi-tenancy controls are implemented to ensure strict data isolation between customers. |
| Data encryption (in-flight) | All data transmitted between the agent and gateway and the cloud are encrypted with TLS v1.2 standards. |
| Data encryption (at-rest) | Resource credentials stored in the Cloud are encrypted using 2048-bit RSA encryption. |
| Authentication | Cloud offers SAML and OAuth2 based authentication. Third-party authentication services are supported, such as OneLogin, Okta, and ADFS. The Cloud supports two-factor authentication. |
| User access management | Extensive role-based access controls are implemented. Access controls are granular to the managed device, user, and feature. | APIs | REST APIs are provided for integration with the cloud. The APIs are backed by OAuth2-based authentication. | Regulatory and Compliance Requirements | Personally-identifiable information (PII) is not collected. OpsRamp is hosted in co-location facilities provided by two United States-based data center providers. Each provider has its own security certifications including SAS and SSAE. |
Data security
An extensive set of security features are provided to ensure that management data is accessed only by authorized users.
| Property | Description |
|---|---|
| Encryption | All sensitive data is encrypted. Customer data, including inventory, metrics, alerts, and tickets, is logically partitioned and stored under the tenant. Customer data is accessible only to authorized tenant users. |
| Role-based access control | Comprehensive, role-based access controls are implemented. User access to devices and actions is controlled by fine-grained permissions. Permissions are assigned based on user roles. |
| Identity management | Multiple options to manage user identity are provided:
|
| Authentication | Two-factor authentication using Yubico YubiKey is provided. |
| Passwords | Standard password practices are followed:
|
Data retention
On contract expiration, the tenant is deactivated. An inactive tenant instance inventory, metrics, and alerts data are available in the passive state in the platform, but monitoring, alerting, and other management functions are no longer available.
Based on mutual agreement, all tenant information from the cloud is deleted. The data archival retention policy provides that deleted tenant data is available in the archival repository for ninety days.
Application access
Role-based access controls support fine-grained access control based on user and user groups, device and device groups, specific features, and resource credentials.
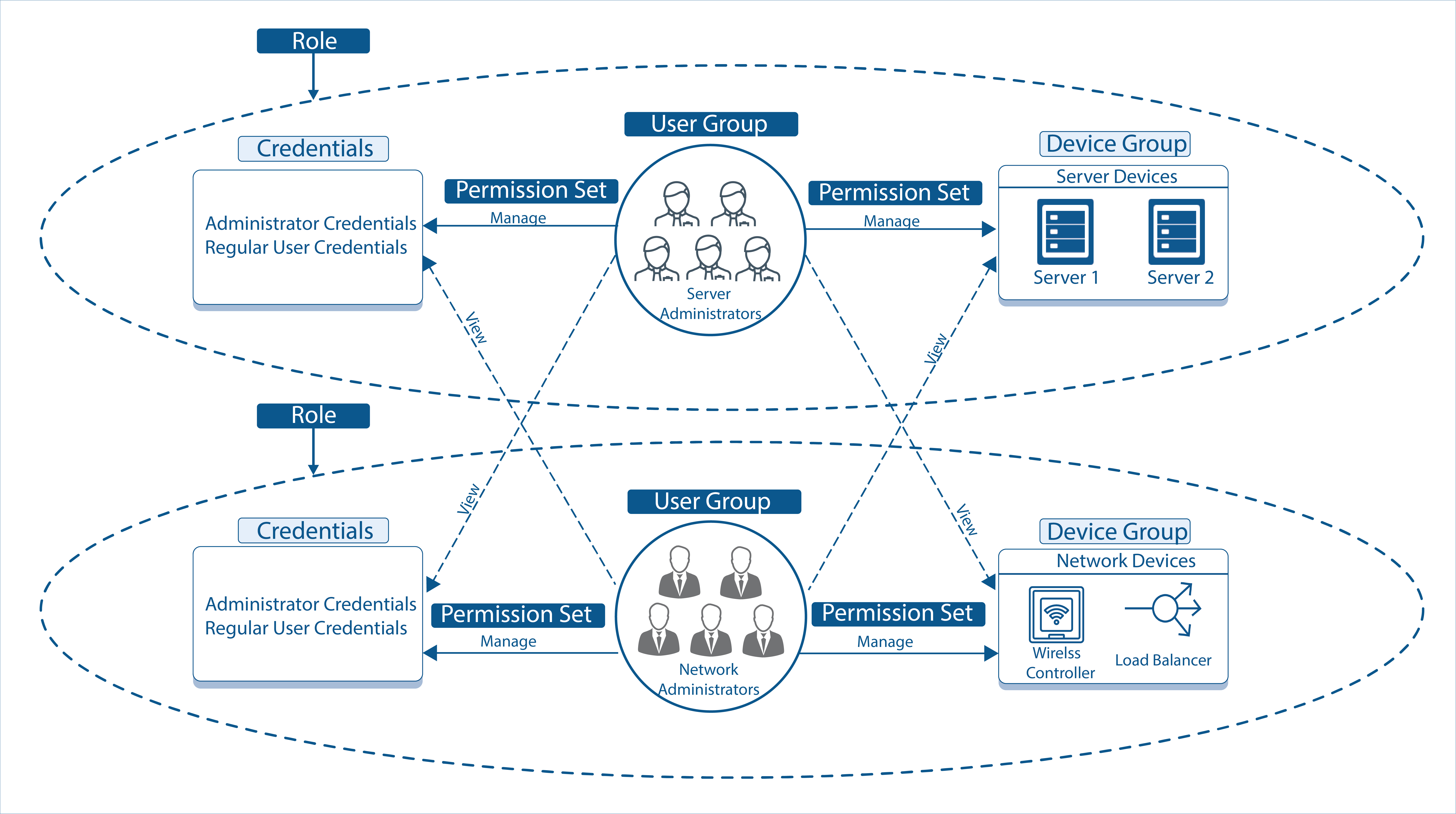
Role-based Access Control
Operations
Operations and development processes follow methodologies that ensure the managed data security, including SOC 2 Type II certification.
| Property | Description |
|---|---|
| Infrastructure management | The platform infrastructure is managed according to industry-standard practices:
|
| Audit processes | Customers can run their own security audit on the agent, gateway, and publicly facing URLs. The cloud is managed using another server instance. Audit recordings of management activities can be provided as needed. |
Production access controls
Physical access to the production area is controlled by biometric and smart card access. Access to data centers is restricted to authorized personnel with 24×7 security monitoring and CCTV surveillance across facilities.
Intrusion prevention
Production environments are protected by 24×7 automated network-level intrusion prevention systems. IP and port-based firewalls continuously monitor authentication logs on Linux servers. Inbound and outbound traffic at various entry points is monitored and vulnerability checks are regularly performed on servers. In a breach, more firewall rules are used to block the specific IP ranges, and passwords, encryption keys, and algorithms are changed.
Password security
All passwords are encrypted. User passwords are a one-way hash for secure password storage. Two levels of password security are provided for data in transit:
- All communication between cloud and providers takes place over TLS.
- Sensitive information in transit is encrypted by unique keys.