Logz.io provides log management and log analysis services. The platform combines ELK as a cloud service and machine learning to derive new insights from machine data.
OpsRamp configuration
Step 1: Install integration
- From All Clients, select a client.
- Go to Setup > Account.
- Select the Integrations and Apps tab.
- The Installed Integrations page, where all the installed applications are displayed. Note: If there are no installed applications, it will navigate to the Available Integrations and Apps page.
- Click + ADD on the Installed Integrations page. The Available Integrations and Apps page displays all the available applications along with the newly created application with the version.
- Search for the application using the search option available. Alternatively, use the All Categories option to search.
- Click ADD on the Logz.io tile.
Inbound (Optional):
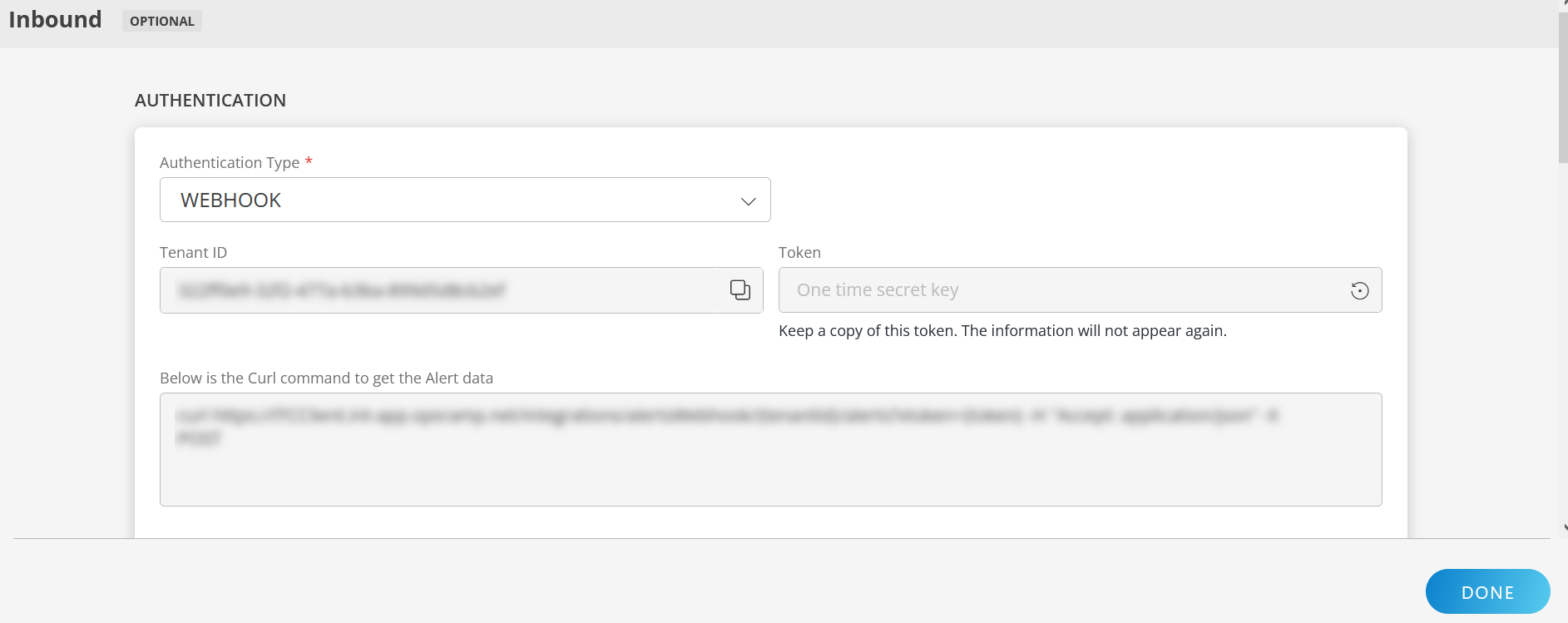
To configure the inbound, follow these steps:
Authentication:
Select the Authentication Type as Webhook.
- Webhook: By default, Webhook is selected as the Authentication Type.
Make a note of Tenant ID, Token and Webhook URL.
These details are used while creating an HTTP Request template during Logz.io configuration.
- Webhook: By default, Webhook is selected as the Authentication Type.
Map Attributes: Map OpsRamp entity attributes with Logz.io attributes.
Click +Add from the Map Attributes section.
From the Add Map Attributes window, enter the below information:
- OpsRamp Entity: Select Alert from the dropdown.
- OpsRamp Property: Select the OpsRamp property from the dropdown.
- Logz.io Entity: Enter the Logz.io entity value in the box and click the +value from the dropdown to add it. You can add multiple values.
- Logz.io Property: Enter the Logz.io property.
Parsing Condition:
- Click +Add and provide the parsing condition:
- Select an operator from the dropdown and enter a value in the fields accordingly. Based on the operator selected, the fields vary.
- Click Save. Click +Add to add more conditions.
Property Values:
- Click +Property Value.
- Enter a value in the Logz.io Property Value box and select the appropriate value from the OpsRamp Property Value dropdown.
The options in the OpsRamp Property Value dropdown appear based on the OpsRamp Property selected. - Click Save.
- Click +Property Value to add more property values.
Default Value: Alternatively, you can enter/select a default value in the box.
Note: To map more attributes, click +Entity.
Click Add Map Attributes. The mapped attributes list is added.
- Click the three dots icon at the end of each row to edit or remove the map attributes.
- Use the Filter option to filter the map attributes.
Additional Settings: Select the Drop alerts from unmanaged resources checkbox if you do not want to trigger alerts from unmanaged resources.
Enrich and Create Alert: Select a process definition from the dropdown. You can customize the incoming alerts according to the properties defined in the process definition.
Click Finish.
The following tables shows the attribute mappings.
| Third-Party Entity | OpsRamp Entity | Third-Party Property | OpsRamp Property | Third-Party Property Value | OpsRamp Property Value |
|---|---|---|---|---|---|
| result.status | alert.currentState | State | Alert | 200 | Success |
| uri_query | alert.serviceName | Service Name | Alert | ||
| search_name | alert.description | Description | Alert | NA | NA |
| app | alert.deviceName | Resource Name | Alert | NA | NA |
| result.req_time | alert.alertTime | Time | Alert | NA | NA |
| search_name | alert.subject | Subject | Alert | NA | NA |
Attributes can be modified at any time.
Logz.io configuration
Step 1: Configure alert endpoints
- Log into Logz.io Admin UI.
- Go to Alerts & Events > Alert endpoints.
- Select +Add endpoint and enter the following (endpoints help with integrating with other notification systems):
- Type: Select Custom.
- Name: Add a unique name.
- Webhook: Paste the OpsRamp-generated Webhook URL.
- Method: POST
- Headers:
content=type=application/json - Body (Optional) box: Enter the payload.
- Click Save.
Example payload
{
"alert_title": "TestCustom",
"alert_description": "",
"alert_severity": "Medium",
"alert_event_samples": [
{
"request" : "/category/software?from=0",
"agent" : "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)",
"minor" : "0",
"auth" : "-",
"ident" : "-",
"os_major" : "7",
"type" : "logzio-demo-logs-apache",
"major" : "9",
"clientip" : "32.204.193.86",
"_logzio_sample_logs" : true,
"geoip" : {
"timezone" : "America/Chicago",
"ip" : "32.204.193.86",
"latitude" : 37.751,
"country_name" : "United States",
"country_code2" : "US",
"continent_code" : "NA",
"location" : [ -97.822, 37.751 ],
"longitude" : -97.822
},
"os" : "Windows 7",
"verb" : "GET",
"message" : "32.204.193.86 - - [11/June/2019:00:25:00 +0000] "GET /category/software?from=0 HTTP/1.1" 200 40 "-" "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)"",
"tags" : [ "_logz_http_bulk_json_8070", "apache-geoip" ],
"referrer" : "-",
"@timestamp" : "2019-11-01T05:55:32.986+0000",
"_logzio_pattern" : 3213531,
"response" : 200,
"bytes" : 40,
"name" : "IE",
"os_name" : "Windows",
"httpversion" : 1.1,
"device" : "Other"
}
{
"request" : "/category/electronics",
"agent" : "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; YTB730; GTB7.2; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; Media Center PC 6.0)",
"minor" : "0",
"auth" : "-",
"ident" : "-",
"os_major" : "7",
"type" : "logzio-demo-logs-apache",
"major" : "8",
"clientip" : "220.186.227.70",
"_logzio_sample_logs" : true,
"geoip" : {
"timezone" : "Asia/Shanghai",
"ip" : "220.186.227.70",
"latitude" : 30.294,
"country_name" : "China",
"country_code2" : "CN",
"continent_code" : "AS",
"region_name" : "ZJ",
"location" : [ 120.1619, 30.294 ],
"real_region_name" : "Zhejiang",
"longitude" : 120.1619
},
"os" : "Windows 7",
"verb" : "GET",
"message" : "220.186.227.70 - - [11/June/2019:00:24:45 +0000] "GET /category/electronics HTTP/1.1" 200 76 "[http://www.google.com/search?ie=UTF-8&q=google&sclient=psy-ab&q=Electronics&oq=Electronics&aq=f&aqi=g-vL1&aql=&pbx=1&bav=on.2,or.r_gc.r_pw.r_qf.,cf.osb&biw=753&bih=548](http://www.google.com/search?ie=UTF-8&q=google&sclient=psy-ab&q=Electronics&oq=Electronics&aq=f&aqi=g-vL1&aql=&pbx=1&bav=on.2,or.r_gc.r_pw.r_qf.,cf.osb&biw=753&bih=548)" "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; YTB730; GTB7.2; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; Media Center PC 6.0)"",
"tags" : [ "_logz_http_bulk_json_8070", "apache-geoip" ],
"referrer" : ""http://www.google.com/search?ie=UTF-8&q=google&sclient=psy-ab&q=Electronics&oq=Electronics&aq=f&aqi=g-vL1&aql=&pbx=1&bav=on.2,or.r_gc.r_pw.r_qf.,cf.osb&biw=753&bih=548"",
"@timestamp" : "2019-11-01T05:55:32.386+0000",
"_logzio_pattern" : 3213531,
"response" : 200,
"bytes" : 76,
"name" : "IE",
"os_name" : "Windows",
"httpversion" : 1.1,
"device" : "Other"
}
{
"request" : "/category/software?from=20",
"agent" : ""Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; YTB720; GTB7.2; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)"",
"minor" : "0",
"auth" : "-",
"ident" : "-",
"os_major" : "XP",
"type" : "logzio-demo-logs-apache",
"major" : "8",
"clientip" : "32.189.100.196",
"_logzio_sample_logs" : true,
"geoip" : {
"timezone" : "America/Chicago",
"ip" : "32.189.100.196",
"latitude" : 37.751,
"country_name" : "United States",
"country_code2" : "US",
"continent_code" : "NA",
"location" : [ -97.822, 37.751 ],
"longitude" : -97.822
},
"os" : "Windows XP",
"verb" : "GET",
"message" : "32.189.100.196 - - [11/June/2019:00:24:35 +0000] "GET /category/software?from=20 HTTP/1.1" 200 90 "/category/software" "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; YTB720; GTB7.2; .NET CLR 1.1.4322; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)"",
"tags" : [ "_logz_http_bulk_json_8070", "apache-geoip" ],
"referrer" : ""/category/software"",
"@timestamp" : "2019-11-01T05:55:31.982+0000",
"_logzio_pattern" : 3213531,
"response" : 200,
"bytes" : 90,
"name" : "IE",
"os_name" : "Windows",
"httpversion" : 1.1,
"device" : "Other"
}
]
}Step 2: Configure alert profiles
Alert profiles are created for establishing filtering rules.
- Go to Logz.io Home and click Kibana.
- Click Create alert and enter the required information.
For Actions, enter the previously configured alert endpoint.
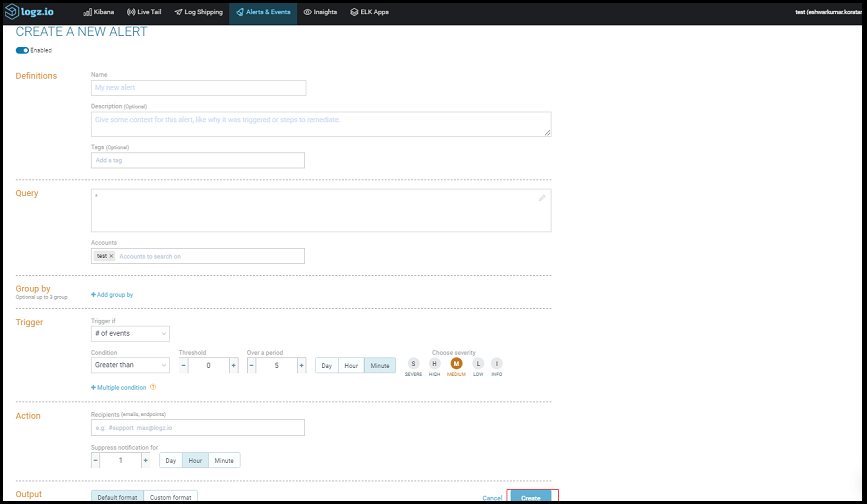
- Click Create.
- To edit alert details: go to Alerts & events > Alert definitions.
- To view the triggered alerts from the Logz.io console: go to Alerts & events > Triggered alerts.
Next steps
- View the alerts in OpsRamp.
- Go to Alerts and search for source name.
- Click an Alert ID to view.