Introduction
RBAC (Role-Based Access Control) ensures that users can view and interact only with resources they are authorized to access in the network topology.
Behavior for Restricted Resources
Network Devices
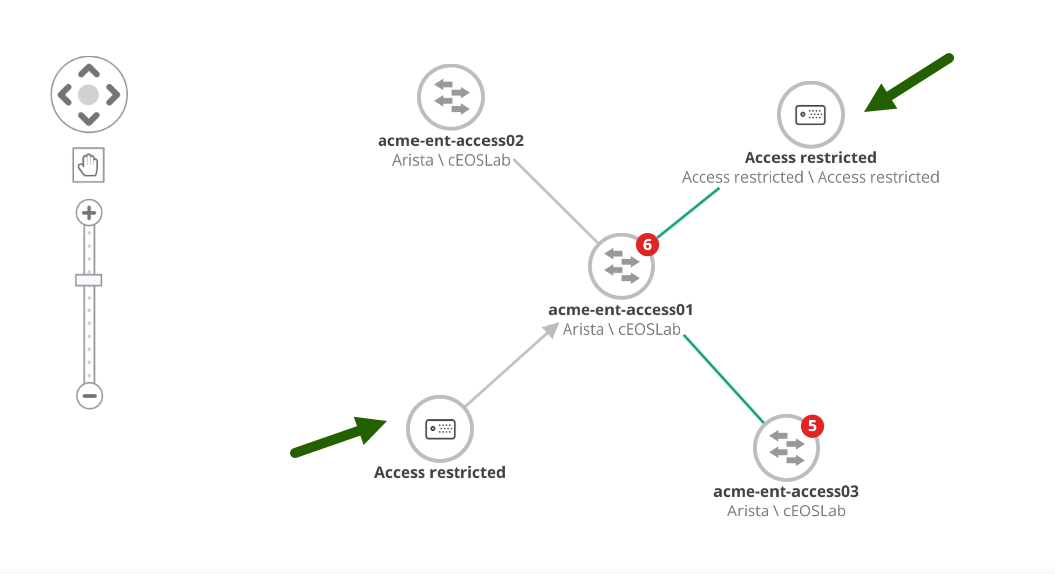
If a user does not have access to a device, its details (such as resource type, host name, make, and model) are hidden and replaced with an “Access Restricted” message.
Resource Groups
- If restricted resources have visible relationships or links, the nodes remain visible but their values are replaced with “Access Restricted”.
- If restricted resources have no visible links or relationships, the nodes are not displayed in the topology view.
Alerts and Availability
Alert counts and availability indicators are disabled for resources the user cannot access, preventing unauthorized interactions.
User Interaction with Restricted Nodes
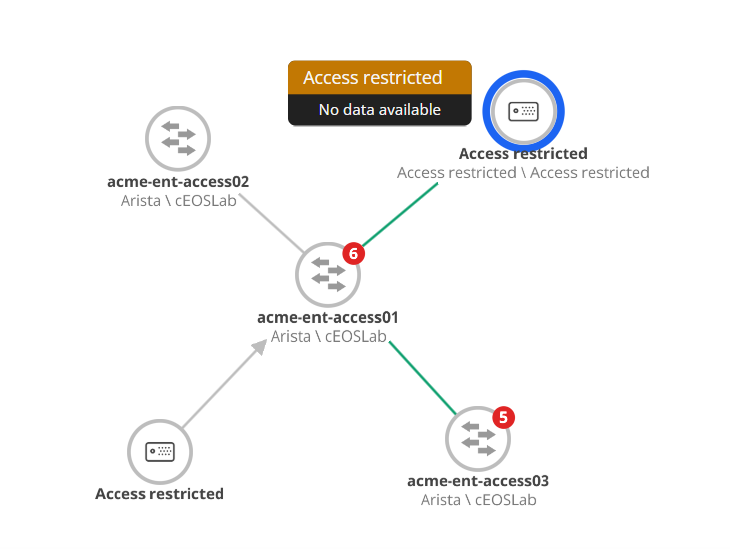
- Hovering: Displays “Access Restricted” and “No data available”.
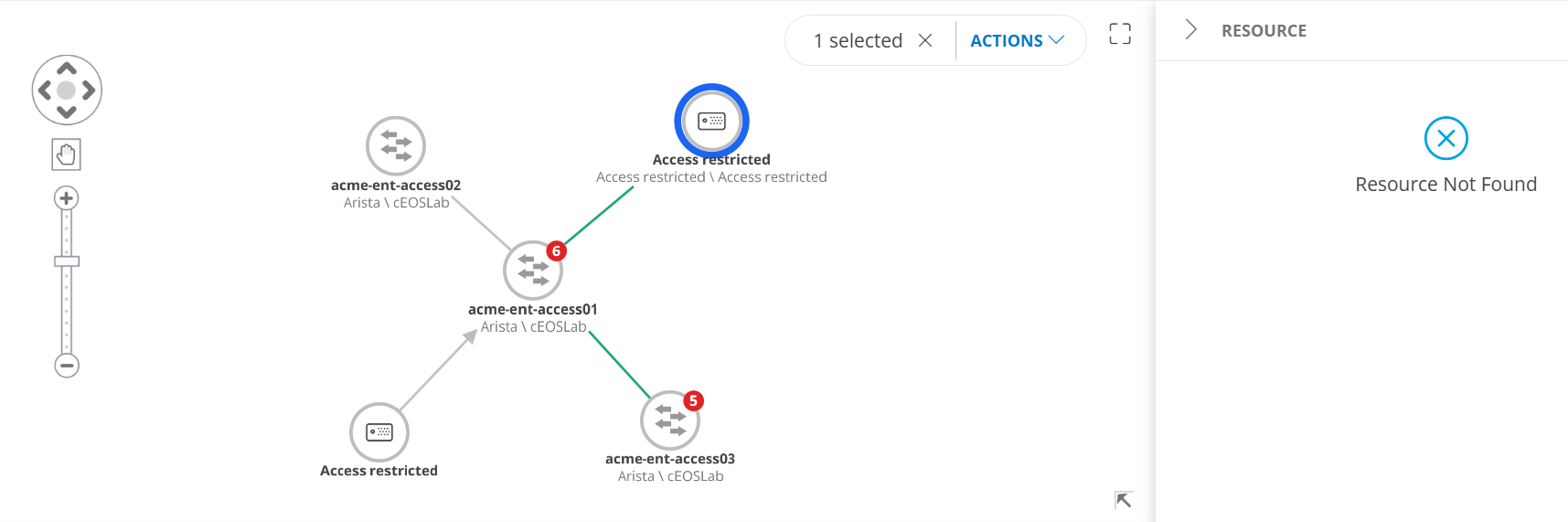
- Clicking: Opens the slide-out with a “Resource Not Found” message.
This ensures sensitive information is protected while maintaining the overall topology structure.