This section guides you through setting up, configuring, and managing the MS SQL integration.
Prerequisites
Prerequisites to be implemented on Gateway:
- OpsRamp Classic Gateway (Linux) 15.0.0 and above.
- OpsRamp Nextgen Gateway 15.0.0 and above.
- Upgrade to the latest Gateway version to ensure comprehensive coverage of recent bug fixes, feature enhancements, and so on.
Prerequisites for Target Cluster or Standalone Nodes
To execute PowerShell cmdlets successfully, ensure the following requirement is met:
- Windows domain User should perform the following to do powershell remoting.
Enable-PSRemoting -Force - Add the Windows domain user to the Remote Management Users group:
net localgroup "Remote Management Users" /add <user> - Add the Windows domain user to the Performance Monitor Users group:
net localgroup "Performance monitor users" /add <user> - Add the OpsRamp Gateway IP to the TrustedHosts list on the target machine to allow PowerShell connections from the gateway:
- To add TrustedHosts use the following command:
- To allow any host:
Set-Item WSMan:\localhost\Client\TrustedHosts -Force -Value * - To allow a specific host:
Set-Item WSMan:\localhost\Client\TrustedHosts -Force -Concatenate -Value <OpsRampGatewayIp>
- To allow any host:
- Set up and restart the WinRM service for the changes to take effect.
- To set up:
Set-Service WinRM -StartMode Automatic - Restart using:
Restart-Service -Force WinRM
- To set up:
- To add TrustedHosts use the following command:
- Ensure that ports 5985 (HTTP) and 5986 (HTTPS) are open.
Note
By default, WS-Man and PowerShell remoting use ports 5985 (HTTP) and 5986 (HTTPS) for remote connections.
Enable the following permissions for non-admin/operator users:
Grant Remote WMI Rights
- Click Start and select Run.
- Enter
wmimgmt.mscand click OK. - Right-click WMI Control (Local) and select Properties.
- Go to the Security tab.
- Select Root and click Security.
- Add the user and grant these permissions:
- Execute methods
- Enable account
- Enable remoting
- Read security
- Click Advanced, select the added user, and click Edit.
- Set Applies to as This namespace and subnamespaces.
- Click OK three times to confirm.
Add User to “Performance Monitor Users” Group
- Click Start and select Run.
- Enter
lusrmgr.mscand click OK. - In the Groups folder, right-click Performance Monitor Users and select Properties.
- Go to the Members tab and click Add.
- Add the required users.
To monitor services like Windows cluster service and MSSQL services (SQL Server, SQL Agent, SQL Browser, and so on.), the user must be part of the Local Administrators group (required for using the
win32_Serviceclass).- If you prefer not to add the user to the local administrators group, configure Security descriptors for service monitoring.
- For details on configuring security descriptors, refer to Enable Windows Service Monitoring.
Grant the Windows domain user read-only access to the cluster using the following command:
Grant-ClusterAccess -User <domain\user> -ReadonlyEnsure that the provided IP address/host name and credentials are valid and accessible for successful integration. To verify connectivity from the gateway, follow these steps:
- Launch PowerShell using the
pwshcommand. - Run the following commands to establish a remote session to your end device:
- {$pw = convertto-securestring -AsPlainText -Force -String "<password>"} - {$cred = new-object -typename System.Management.Automation.PSCredential -argumentlist "<username>", $pw} - {$session = new-pssession -computername "<ipAddress>" -credential $cred -Authentication Negotiate -ErrorAction Stop} - {session.state}- Launch PowerShell using the
Note
The session state should be open.SQL authorization permissions:
- Ensure the SQL Server instance accepts connections on the database port and that firewall rules allow traffic over this port.
- OpsRamp supports mixed authentication for JDBC connections, including (both NTLM and SQL Server authentication).
- The user account used for monitoring must have the following minimum privileges:
Server Role:
public(default server role)
Securables:
Grant the following permissions to the monitoring user for connectivity and read-only access to SQL instances and databases:- CONNECT TO ANY DATABASE:
GRANT CONNECT ANY DATABASE TO <user> - CONNECT TO SQL SERVER:
GRANT CONNECT SQL TO <user> - SELECT ALL USER SECURABLES:
GRANT SELECT ALL USER SECURABLES TO <user> - VIEW ANY DATABASE:
GRANT VIEW ANY DATABASE TO <user> - VIEW ANY DEFINITION:
GRANT VIEW ANY DEFINITION TO <user> - VIEW SERVER STATE:
GRANT VIEW SERVER STATE TO <user>
- CONNECT TO ANY DATABASE:
Configure and Install the MS SQL Cluster Integration
- From All Clients, select a client.
- Go to Setup > Account.
- Select the Integrations and Apps tab.
- The INSTALLED INTEGRATIONS page, where all the installed applications are displayed.
Note: If there are no installed applications, it will navigate to the Available Integrations and Apps page. - Click + ADD on the INSTALLED INTEGRATIONS page. The AVAILABLE INTEGRATIONS AND APPS page displays all the available applications along with the newly created application with the version.
Note: You can even search for the application using the search option available. Also you can use the All Categories option to search. - Click ADD in the MS SQL Cluster application.
- In the Configurations page, click + ADD. The Add Configuration page appears.
- Enter the following BASIC INFORMATION:
| Field Name | Field Type | Field Dependency | Description |
|---|---|---|---|
| Name | String | NA | Enter the name for the integration. |
| MSSQL Type* | Dropdown | N/A | Select the type of Microsoft SQL Server instance you are integrating. The options availble are:
|
| IpAddress/HostName* | Text | N/A | If the MSSQL Type is set to CLUSTER, enter the IP address or hostname of the Windows cluster. If set to STANDALONE, enter the IP address or hostname of the individual node instead. |
| MSSQL Cluster Type | Dropdown | Appears only when Cluster is selected in the MSSQL Type field. | Select the type of SQL Server cluster configuration being integrated. The options available are:
|
| MSSQL Cluster / Node Credentials* | Dropdown | N/A | Provide the Windows authentication credentials required to connect to the Windows cluster hosting the SQL Server cluster, or to the individual nodes in the case of a standalone SQL Server deployment. You can either select from the dropdown if the credentials are existing. Else click +ADD to create credentials. In the ADD CREDENTIAL window enter the following:
|
| SQL Server Authentication Mode | Checkbox | N/A | Enable this option to provide SQL Server credentials if the specified Windows credentials do not have sufficient SQL Server access rights.
|
| SQL Server Credentials | Dropdown | This field is displayed only when the SQL Server Authentication Mode checkbox is selected. | Select the SQL Server credentials from the dropdown. You can either select from the dropdown if the credentials are existing. Else click +ADD to create credentials. In the ADD CREDENTIAL window enter the following:
|
| App Failure Notifications | Checkbox | N/A | This checkbox is used to confirm whether a notification should be sent in the event of an app failure due to authentication or connection-related exceptions.
|
| Request Timeouts | Checkbox | N/A | Selecting this checkbox enables you to configure the timeout settings for NativeBridge connections and script execution requests made by the integration to the end device. |
| Connection TimeOut In Mins | Dropdown | This field appears only if the Request Timeouts checkbox is selected. | Select the maximum time, in minutes, that the integration should wait while establishing a connection with the nativeBridge. Default value: 10 minutes. |
| Connection Request TimeOut In Min | Dropdown | This field appears only if the Request Timeouts checkbox is selected. | Select the maximum time, in minutes, required to process a NativeBridge HTTP call, from sending the request to receiving the response. Default value: 10 minutes. |
| Socket Timeout In Mins | Dropdown | This field appears only if the Request Timeouts checkbox is selected. | Select the maximum allowable time of inactivity between two data packets during data exchange with the server. Default value: 10 minutes. |
| Script Execution TimeOut In Mins | Dropdown | This field appears only if the Request Timeouts checkbox is selected. | Select the maximum time, in minutes, that the integration should wait while establishing a connection with the nativeBridge. Default value: 10 minutes. |
- Select the below mentioned Custom Attribute:
| Field Name | Field Type | Field Dependency | Description |
|---|---|---|---|
| Custom Attribute | Dropdown | N/A | Select the custom attribute from the dropdown. |
| Value | Dropdown | N/A | Select the value from the dropdown. |
Note: The custom attribute that you add here will be assigned to all the resources that are created by the integration. You can add a maximum of five custom attributes (key and value pair).
- In the RESOURCE TYPE section, select:
- ALL: All the existing and future resources will be discovered.
- SELECT: You can select one or multiple resources to be discovered.
- In the DISCOVERY SCHEDULE section, select Recurrence Pattern to add one of the following patterns:
- Minutes
- Hourly
- Daily
- Weekly
- Monthly
- Click ADD.

Note
Sample values shown in the configuration fields are for illustration purposes only. Use your actual integration details when configuring.Now the configuration is saved and displayed on the configurations page after you save it.
Note: From the same page, you may Edit and Remove the created configuration.
- Click Next.
- Below are the optional steps you can perform on the Installation page.
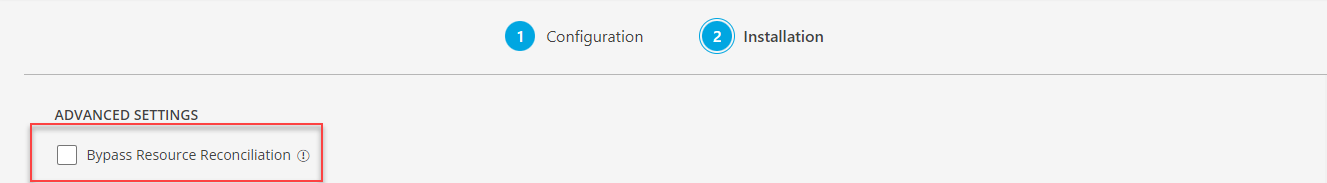
Under the ADVANCED SETTINGS, Select the Bypass Resource Reconciliation option, if you wish to bypass resource reconciliation when encountering the same resources discovered by multiple applications.
Note: If two different applications provide identical discovery attributes, two separate resources will be generated with those respective attributes from the individual discoveries.
- Click +ADD to create a new collector by providing a name or use the pre-populated name.
- Select an existing registered profile.
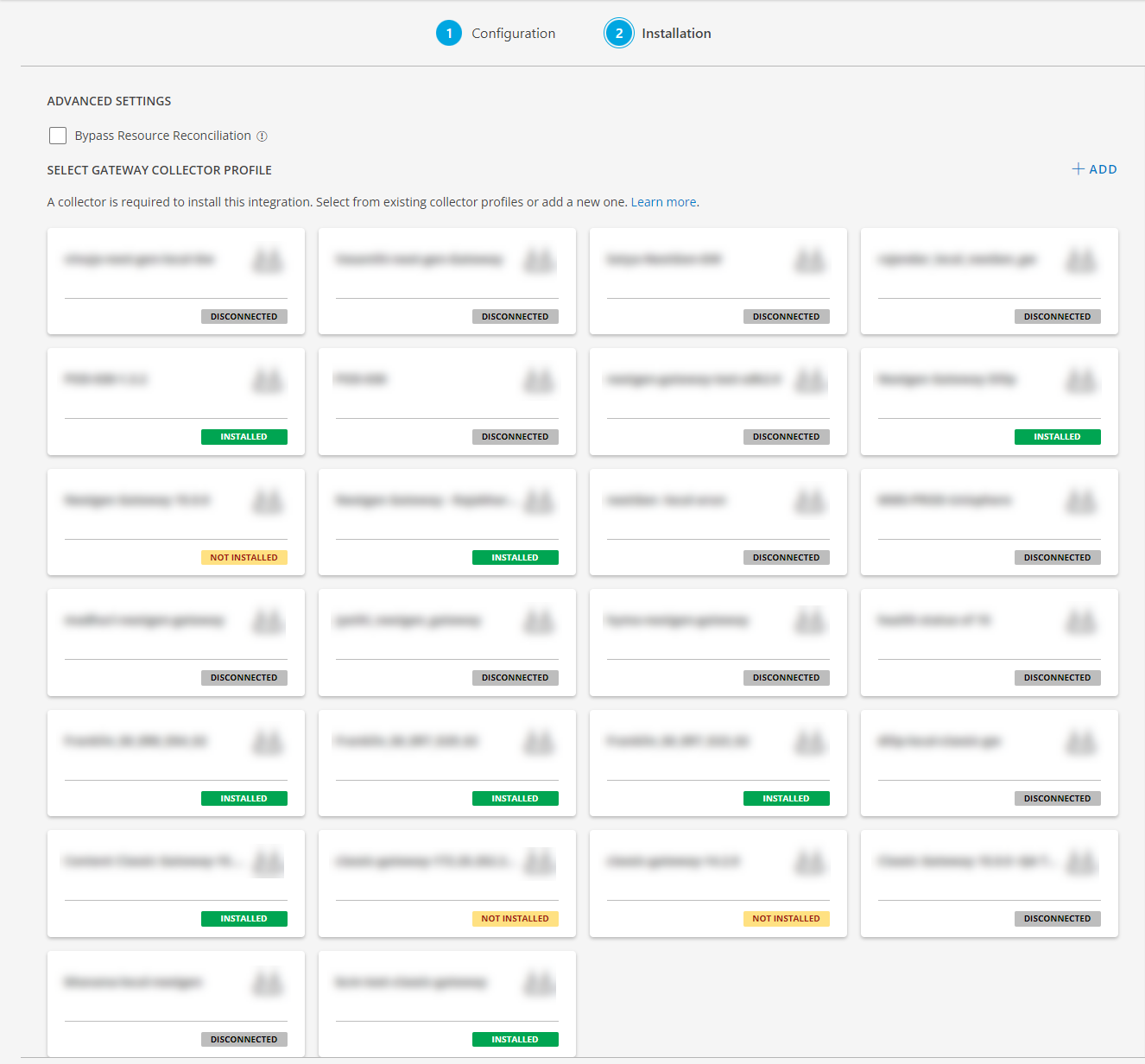
- Click FINISH.
The application is now installed and displayed on the INSTALLED INTEGRATION page. Use the search field to find the installed application.
Modify the Configuration
See Modify an Installed Integration or Application article.
Note: Select the MS SQL Cluster application.
View the MS SQL Cluster Details
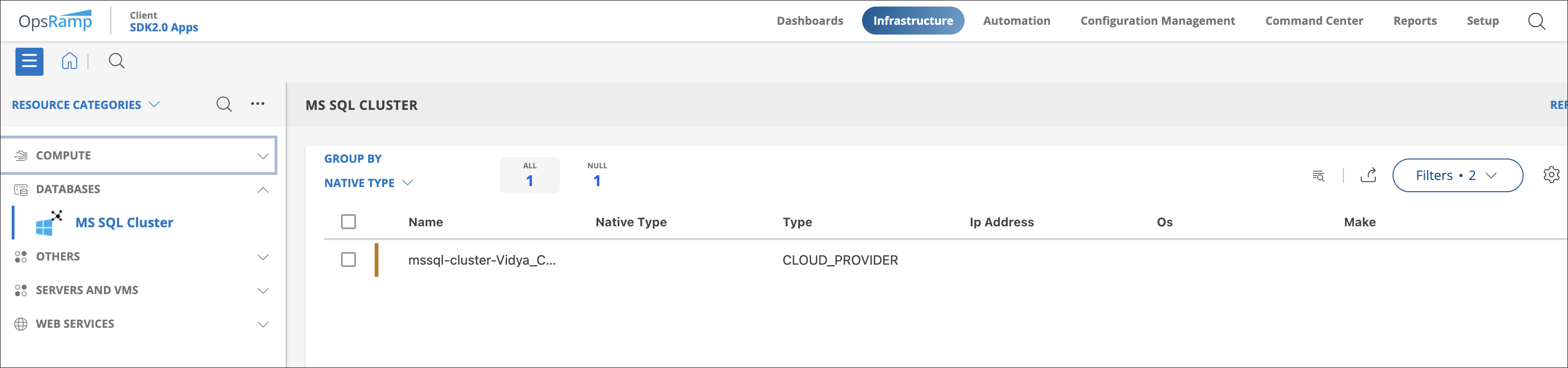
- Navigate to Infrastructure > Search > DATABASES > MS SQL Cluster.
- Select the application on the MS SQL Cluster page.
- The RESOURCE page appears from the right.
- Click the ellipsis (…) on the top right and select View Details.
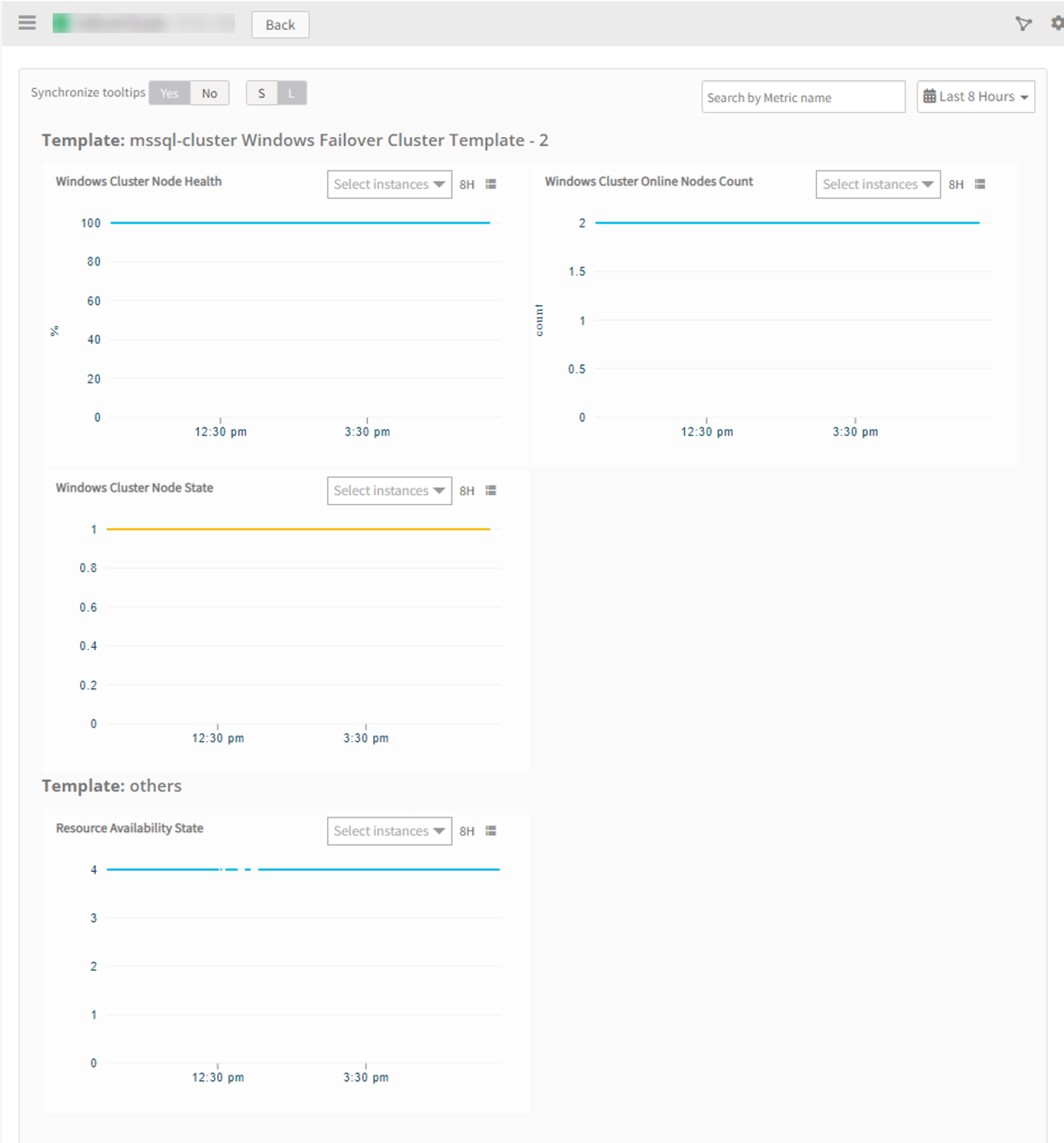
View resource metrics
To confirm MS SQL Cluster monitoring, review the following:
- Metric graphs: A graph is plotted for each metric that is enabled in the configuration.
- Alerts: Alerts are generated for metrics that are configured as defined for integration.